
This blog describes the design and implementation of an identity-aware agentic AI system. The goal is to build an AI model that not only understands and interacts based on user identity but can also trigger relevant actions (agentic behavior) based on user input and their roles. The system integrates:
- User Authentication & Identity Management (using solutions such as Firebase Auth or Auth0)
- Database & User Profiles (leveraging PostgreSQL or Supabase)
- AI Integration (with APIs like OpenAI’s ChatCompletion and tools like LangChain)
- Agentic Actions (through generic API calls like SMS notifications or scheduling events)
This design is inspired by the modern architecture adopted by several Indian tech companies, which emphasizes security, modularity, and scalability.
System Overview
Key Modules
Identity Management:
Handles user registration, login, and session management using third-party authentication services.
User Profile Database:
Stores user-specific data (profiles, preferences, etc.) using relational databases.
AI Integration Module:
Communicates with the OpenAI API (or similar models, such as Hugging Face Transformers) to generate responses and utilizes frameworks like LangChain for context management.
Agentic Actions Module:
Maps AI-decided actions to function calls that trigger external services (e.g., sending SMS, scheduling calendar events).
High-Level Architecture Diagram
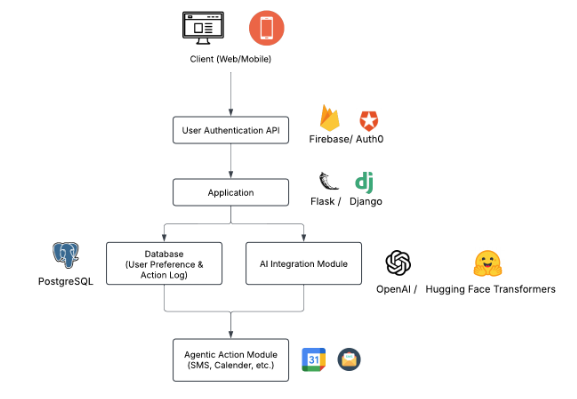
Detailed Component Designs
3.1 Identity Management
Purpose:
Ensure that only authenticated users can access the AI functionalities. This can be achieved using Firebase Auth, Auth0, or similar services.
Key Concepts:
1. Token Verification
Authentication should be token-based, ensuring that each request is verified before accessing AI functionalities. The strategy includes
- Using JWTs: Clients authenticate and receive a JWT, which is passed in API requests for validation.
- Backend Validation: The server verifies JWTs against the authentication provider (e.g., Firebase, Auth0) to confirm user authenticity.
- Role & Permission Checks: Tokens should include claims that define the user’s access level (e.g., admin, user, viewer).
Best Practices:
- Use short-lived tokens to minimize security risks
- Implement token revocation mechanisms for compromised accounts.
2. Secure Session Management
To maintain secure and persistent user sessions:
- Token Expiry & Refresh: Implement short-lived access tokens and refresh tokens to avoid persistent session risks.
- Secure Storage: Store tokens securely—use HttpOnly cookies for web applications and secure enclaves or storage for mobile applications.
- Multi-Factor Authentication (MFA): Strengthen security by requiring an additional verification step.
Best Practices:
- Use refresh tokens securely to extend sessions without frequent logins.
- Prevent session hijacking with token rotation and device-based authentication tracking.
3.2 Database & User Profiles
Purpose:
Manage and persist user profiles and preferences. Many Indian enterprises utilize robust RDBMS solutions, such as PostgreSQL, which are sometimes managed through platforms like Supabase.
Key Considerations:
1. Schema Design
A well-structured schema ensures efficient data retrieval and management. The user profile table should include:
- User ID (Primary Key)—Unique identifier for each user.
- Name & Email—standard user identity fields.
- Preferences—Storing user settings, such as theme, language, or notification preferences.
- Roles & Permissions—for access control and authorization.
- Timestamps—for tracking account creation and last login activity.
Best Practice:
Utilize JSONB fields in PostgreSQL for storing dynamic user preferences, enabling flexibility without requiring frequent schema alterations.
2. Data Security
Securing user data is crucial, particularly when handling sensitive personal information. Key security measures include
Encryption:
- Store passwords using bcrypt hashing.
- Encrypt sensitive fields (e.g., email, contact details) using AES encryption or PostgreSQL’s pgcrypto extension.
Access Control & Compliance:
- Implement role-based access control (RBAC) to restrict access to sensitive data and information.
- Use column-level encryption to protect personally identifiable information (PII).
- Ensure compliance with India’s Digital Personal Data Protection Act (DPDPA) and GDPR for international applications.
Best Practice:
Utilize Supabase Row-Level Security (RLS) to enforce access policies at the database level, ensuring users can only access their data.
3.3 AI Integration Module
Purpose:
Integrate with an AI model (e.g., OpenAI’s ChatCompletion API) to generate responses and maintain context using tools like LangChain.
Key Concepts:
1. Prompt Engineering
To ensure AI responses are relevant, personalized, and aligned with the user’s identity, design effective prompts that include critical context.
- Incorporate User Identity: Design prompts that integrate user data, such as preferences or previous interactions, to tailor the AI response.
- Example: For a user profile with preferences for a specific language or tone, you could craft prompts like, “Respond to the user in a friendly, professional tone, as they prefer concise answers.”
- Use Dynamic Prompts: Modify prompts in real-time based on user inputs to ensure continuous relevance. This can involve adding more context as the conversation progresses.
Best Practice:
Build reusable prompt templates that can dynamically adapt to the user-provided context, thereby maintaining consistency and personalization across interactions.
2. Context Management
To foster meaningful, ongoing conversations, it is essential to maintain a conversation history and utilize this information to inform future responses. This ensures that the AI model provides contextually aware replies.
- Conversation Memory: Store and access conversation history in a database or session storage. This allows the system to reference past interactions and prevent the AI from losing track of ongoing discussions.
- Token Management: Be mindful of token limits (e.g., OpenAI’s 4096 token limit for ChatCompletion). Prioritize conversation history by trimming or summarizing past exchanges to stay within limits while maintaining relevant context.
- Session Context: Track specific attributes tied to the user’s current session, such as active tasks, preferences, or recent interactions, to maintain a coherent flow of conversation.
Best Practice:
Implement session-based context that is refreshed at regular intervals or in response to specific triggers (e.g., user requests for new information.
3. Integration with AI Models
When integrating with the ChatCompletion API or any AI model, ensure smooth data flow and interaction between the front-end and back-end systems.
- API Calls: Design API endpoints that interact with the AI model and return generated responses based on the current user context.
- Error Handling & Fallbacks: Implement robust error-handling strategies for AI integration, such as fallback responses when the AI model fails or produces inaccurate results.
Best Practice:
Integrate caching mechanisms to store commonly asked queries and their corresponding responses, enabling faster retrieval and reducing API call costs while improving response times.
3.4 Agentic Actions Module
Purpose:
Define and execute actions based on AI decisions. These actions are generic, meaning you can later integrate specific APIs (e.g., Twilio for SMS, Google Calendar for events). This module now integrates with the database to record every action, enabling the system to learn from past actions and make more informed decisions.
Design Considerations:
1. Action Mapping
To facilitate seamless execution of actions, we can map action names to their corresponding function calls using a dictionary or configuration file.
- Dictionary/Mapping Structure: Create a central dictionary that associates action names with the appropriate function or API call.
ACTION_MAP = {
“send_sms”: send_sms,
“create_event”: create_event,
“notify_user”: notify_user, 3
- Action Handler: Design a central handler that reads the action name from the AI’s response and looks it up in the action map. Once found, the corresponding function is called.
Dynamic Execution: If new actions are required, simply add new key-value pairs to the dictionary or configuration.
Best Practice:
To avoid overloading the dictionary with too many hard-coded entries, maintain action mappings in a separate, external configuration file (e.g., JSON, YAML) that can be updated as needed.
2. Extensibility
To ensure the system can easily evolve, consider building an extensible architecture that allows new actions to be added without requiring modifications to the core logic.
- Modular Action Functions: Keep individual action functions decoupled, ensuring each function is responsible for a specific task, such as sending an SMS or creating a calendar event. This makes it easy to swap, extend, or replace functions as new external APIs or actions are required.
- Plug-in Design: Consider using a plug-in architecture for adding new actions. Each plugin (action) can be packaged as a module that the system dynamically imports at runtime.
- Version Control for Actions: Utilize version control for actions, particularly when you anticipate frequent updates to action functions, such as changes in API calls or the introduction of new features for specific integrations. This helps manage backwards compatibility and ensures the system can handle versioned actions.
Best Practice:
Use a dynamic import system or dependency injection to load new actions at runtime based on configuration, ensuring that you don’t need to restart the system when adding or modifying actions.
3. Integration with Database for Action Logging
To enable the system to learn from past actions, logging every executed action is essential. The action log will contain information about the action type, the user who initiated it, and the outcome (success or failure).
- Database Schema for Action Logs:
Fields may include:
- Action ID (Primary Key)
- Action Name (e.g., “send_sms”, “create_event”)
- User ID (to track which user initiated the action)
- Timestamp (when the action was executed)
- Result (success or failure)
- Response Details (any relevant API response or error message)
- Reinforcement Learning:
Over time, analyze action logs to determine which actions yield the best outcomes. The system can utilize this data to enhance decision-making or develop machine learning-based reinforcement learning models that refine the AI’s decision-making.
Best Practice:
Implement asynchronous logging to prevent delays in action execution. This can be done by queuing logs to a separate worker or task queue (e.g., Celery in Python).
4. Example Actions
As the system grows, you should integrate more specific APIs. Here are a few examples:
- SMS via Twilio: Send an SMS to a user when a particular action is triggered.
- Email Notification via SendGrid: Notify the user when an event is created or updated.
- Google Calendar Integration: Create events or reminders on Google Calendar based on user inputs.
- Slack Messaging: Send updates to a team Slack channel when specific actions are executed.
For each action, ensure you create a corresponding handler function that integrates with the relevant API.
4. Implementation Considerations
Security:
- Use HTTPS for all communications.
- Ensure proper validation of tokens and user inputs.
- Follow best practices for database security, including the use of parameterized queries and encryption.
Scalability & Modularity:
- Keep components loosely coupled.
- Use containerization (e.g., Docker) to deploy services independently.
- Leverage cloud platforms that Indian tech companies commonly use for production-grade deployments.
Logging & Monitoring:
- Integrate logging to track API calls and errors.
- Utilize monitoring tools for system health, such as Prometheus and Grafana.
Testing & Documentation:
- Write unit tests for critical modules.
- Maintain clear documentation and code comments to ensure future developers can easily understand and maintain the code.
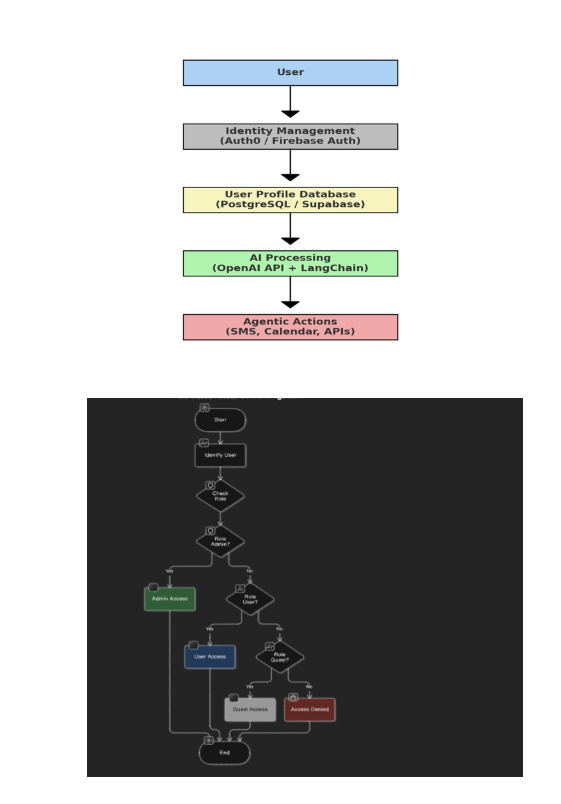
5. System Architecture & Flow
Below is the high-level system architecture, which illustrates the interaction between different components.
Example: Role-Based Access Control (RBAC) for HR in an Identity-Aware Agent AI System
Scenario Overview
The AI system must handle various user roles with distinct permissions. One such role is HR Manager, who requires access to employee data, interview scheduling, and offer management, but should not have access to financial records or technical reports.
HR Role and Responsibilities
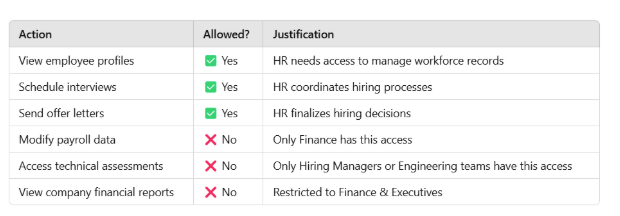
The HR Manager interacts with the AI system to:
- View Employee Profiles – Access basic details, including name, position, department, and contact information.
- Schedule Interviews – Set up interview slots with candidates and notify interviewers.
- Send Offer Letters – Generate and send job offers to selected candidates.
However, they should not have access to:
- The Finance department manages salary and payroll details.
- Performance evaluations of technical employees (handled by Engineering/Management).
- Company-wide strategic documents.
How the System Implements HR Role-Based Access
1. User Authentication and Role Assignment
- When an HR Manager logs in, the system checks their identity using authentication services (e.g., Firebase Auth, Auth0).
- After authentication, their role (HR Manager) is retrieved from the database.
- The system loads predefined permissions assigned to this role.
2. Role-Based Permission Control
The AI determines what an HR Manager can or cannot do based on predefined rules:
3. AI’s Role in Identity-Aware Decision Making
The AI system plays a key role in enforcing RBAC by:
- Validating Requests: When an HR user requests an action, the AI checks their role before proceeding.
- Guiding Users: If an unauthorized request is made, the AI responds with:
“You do not have permission to access payroll data. Please contact the Finance team.” - Automating Workflows: Based on HR’s request, the AI can trigger actions like interview scheduling or offer letter generation.
Example Interaction with AI
👤 HR Manager: “Schedule an interview for Jane Doe on March 15th at 10 AM.”
🤖 AI: “Confirmed. Jane Doe’s interview is scheduled for March 15th at 10 AM. A calendar invite has been sent to the panel.”
👤 HR Manager: “Show me John Smith’s salary details.”
🤖 AI: “Sorry, you don’t have access to salary information. Please contact the Finance department.”
4. Workflow for HR-Specific Actions
a) Viewing Employee Profiles
- The AI verifies the user’s role as “HR Manager.”
- If authorized, it retrieves employee data (excluding sensitive salary details).
- The AI formats and presents the information in a structured way.
b) Scheduling Interviews
- The HR Manager selects a candidate and a preferred time slot.
- The AI system checks availability and schedules the interview.
- It automatically notifies both the candidate and the interview panel.
c) Sending Offer Letters
- The AI generates an offer letter template with predefined terms and conditions.
- HR reviews and approves it.
- The AI system sends it to the candidate via email.
5. Security and Compliance Measures
- Access Logs: The system logs every action taken by HR to ensure transparency and prevent unauthorized access.
- Role-Based Restrictions: Even if an HR user tries to access restricted data, the AI blocks the request.
- Data Encryption: Sensitive employee data is encrypted to prevent leaks.
- Regulatory Compliance: The system adheres to data protection laws, including the General Data Protection Regulation (GDPR) and India’s Information Technology Act








