
Key Takeaways
- Enterprises often have multiple automation tools (LLMs, RPA bots, scripts), but without coordinated control, these agents operate in silos—leading to duplicated effort, conflicts, and missed escalations.
- A true MACC enables real-time task allocation, agent intent arbitration, contextual memory, and escalation handling—providing dynamic coordination, not just visibility.
- Dividing execution, coordination, and oversight responsibilities allows teams to enforce policies, handle exceptions, and support auditability without breaking operational flows.
- A2A protocols, task state schemas, and message normalization are essential to ensure agents with different tech stacks and interfaces can collaborate meaningfully.
- Building a MACC means embedding intelligence, resilience, and governance into the enterprise operating model. It’s a long-term enabler for digital agility, not just a quick automation win.
In most enterprise IT spaces today, operational automation is scattered. A bot here, a scheduling workflow there, maybe an LLM-based assistant bolted onto a customer support app. Each “agent”—whether rule-based, ML-driven, or LLM-enabled—does its job in isolation. What’s missing is coordination. Not orchestration in the BPMN sense, but actual coordination—the kind you need when multiple semi-autonomous actors are working toward overlapping goals in real time. That’s where the concept of a Multi-Agent Control Center (MACC) comes in.
This isn’t a dashboard. It’s not a script runner. And it’s not another static workflow orchestrator with fancy UI layers. It’s a living system—a shared operational command fabric where agents can observe, plan, interact, and adapt based on what others are doing, what the business environment demands, and what constraints or escalation paths exist.
Building such a system isn’t a weekend sprint. It’s an architectural undertaking. But if done right, it reshapes how enterprises handle complexity—not just automate it.
Also read: Framework for Building a Multi-Agent Control Center for Enterprise Operations
The Imperative for Multi-Agent Coordination in Enterprises
Most enterprises already have multiple automation actors in play:
- RPA bots handling data entry.
- LLM-powered assistants are generating first drafts or answers.
- Event-based scripts respond to triggers from monitoring tools.
- ML models embedded in fraud detection or pricing flows.
The problem? They don’t talk to each other meaningfully. Worse, they sometimes duplicate work or conflict in decision paths.
When workflows span multiple departments—say, sales triggering fulfillment, which then cascades into finance and inventory—you can’t afford for automation actors to behave like siloed freelancers. You need operational cohesion.
A Multi-Agent Control Center is the coordination layer that ensures:
- Agents don’t step on each other’s toes.
- Context is shared fluidly across automation layers.
- Policies, not just processes, govern agent behavior.
- There’s a human in the loop when needed, not always or never.
Without such a framework, complexity scales faster than control.
What does a Multi-Agent Control Center do?
Let’s be blunt: many so-called “agent hubs” are glorified logs or dashboards. That’s not what we’re discussing here.
A proper Multi-Agent Control Center (MACC) performs:
- Real-time agent monitoring: Tracks actions, states, intents, and errors across heterogeneous agents.
- Dynamic task allocation: Assigns tasks based on skills, availability, policy, or real-time optimization logic.
- Intent resolution: Detects when agents are pursuing conflicting goals and arbitrates.
- Escalation routing: Routes failures, ambiguity, or policy violations to appropriate fallback paths (human or synthetic).
- Memory management: Maintains contextual memory across tasks, so agents don’t repeat or contradict actions.
Think of it like air traffic control. Every aircraft (agent) is competent on its own—but chaos ensues without coordination, especially during unexpected turbulence or reroutes.
Key Architectural Components
There’s no one-size-fits-all, but a robust MACC generally includes:
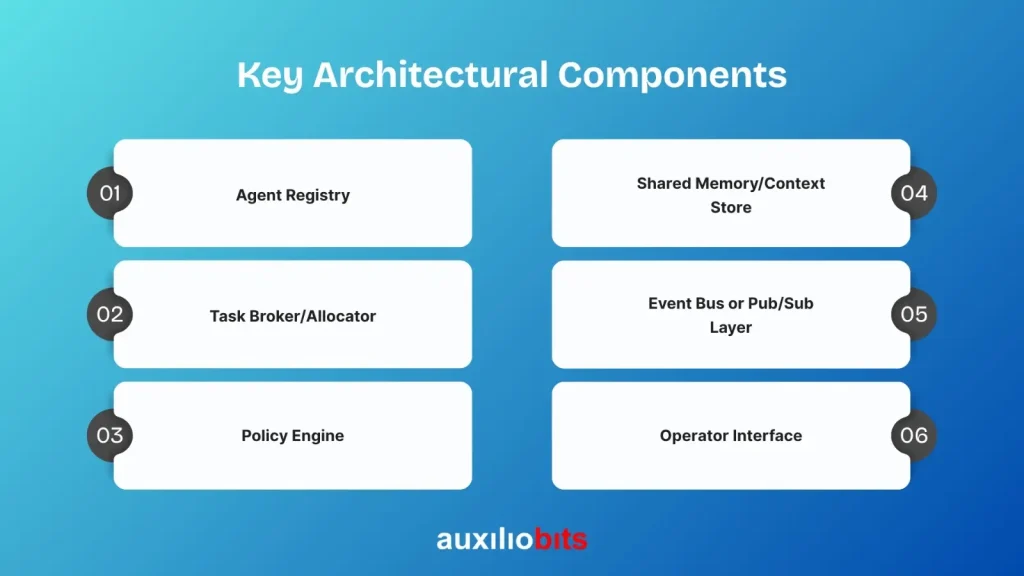
Agent Registry:
Metadata about all active agents: capabilities, interfaces, constraints, ownership, trust level.
Task Broker/Allocator:
Handles incoming goals, decomposes them (if needed), and assigns subtasks to appropriate agents.
Policy Engine:
Applies governance, business rules, and exception handling logic across all agent activities.
Shared Memory/Context Store:
Maintains operational context, not just past logs—enabling agents to reference decisions, states, or partially completed actions.
Event Bus or Pub/Sub Layer:
Enables loosely coupled communication and reactive behavior between agents.
Operator Interface:
Not just for viewing logs. This interface allows operators to intervene, redirect tasks, override agents, or inject new goals midstream.
These components aren’t just technical—they reflect operational maturity. When you see enterprises wiring together these components, you know they’re not just doing “automation” anymore. They’re building operational cognition.
Coordination Framework: Layers and Responsibilities
A well-designed MACC framework separates concerns across three layers:
a. Execution Layer:
This is where the agents live—be they LLMs, RPA bots, Python scripts, or API-driven workers. The MACC should treat these as “pluggable actors,” abstracting their internal mechanics.
b. Coordination Layer:
The true heart. Responsible for:
- Assigning agents to subgoals.
- Tracking agent availability and trust levels.
- Handling retries, delegation, or agent switching mid-task.
c. Oversight Layer:
This includes policy enforcement, escalation management, auditability, and system health monitoring. This layer also supports human inputs when ambiguity or risk is detected.
Quick side note: Many teams are tempted to collapse these layers “for simplicity.” That works until the third month, when Legal asks for an audit trail that includes which agent declined a task due to incomplete context. Build separation early.
Communication Protocols and Agent Interoperability
A surprising number of MACC initiatives fail here. Agents are built in silos and speak incompatible dialects—JSON for one, Protobuf for another, REST for some, socket-based for others.
You need standardized communication scaffolding:
- Agent-to-Agent Protocol (A2A): Define a universal contract for intent declaration, task acceptance, rejection, and handoff. Google’s A2A protocol or open-source equivalents can help.
- Message Normalization: All agent messages must be normalized via a canonical schema—especially if LLMs are involved.
- Task State Encoding: Each task must carry structured metadata: who owns it, what the status is, dependencies, deadlines, and fallback plans.
Tip: Use a conversational protocol layer only when necessary. Don’t turn every handoff into an LLM-based conversation—it’s elegant but brittle. Sometimes a good old task queue with metadata is all you need.
Governance, Risk, and Escalation Models
Agents can be helpful but also dangerous. Especially when they act without context or proper limits. A robust MACC framework must encode:
- Confidence thresholds: Below a certain confidence score, agents must defer to oversight or peers.
- Role-based access control (RBAC): Not all agents should do everything. Some can read PII; others can’t. Some can write to ERP systems; others must request via proxies.
- Escalation trees: When things go wrong—unclear inputs, conflicting decisions, repeated failures—have a tree of fallback actions, not just an alert to Slack.
- Audit trails: Every decision, override, and delegation must be traceable. This isn’t just for compliance; it helps in debugging brittle workflows.
And no, a fancy agent log UI does not count as governance.
Tooling, Stack Choices, and Integration Patterns
Let’s be real: most enterprises don’t have the luxury of greenfield builds. So a MACC must integrate with:
- Legacy systems (SAP, Oracle, etc.)
- Cloud-based tools (ServiceNow, Salesforce)
- Homegrown APIs
- RPA vendors (UiPath, Power Automate)
- LLM services (OpenAI, Azure, Claude, etc.)
Tooling-wise, here are some battle-tested patterns:
- LangGraph for LLM agent orchestration with memory and branching.
- Temporal.io or Prefect for task coordination.
- Redis or vector databases for fast contextual memory.
- Policy-as-code tools like OPA (Open Policy Agent) are used to encode governance.
- Event routers (e.g., Kafka or NATS) for scalable, async coordination.
Whatever you pick, ensure two things:
- Agents don’t need to know about each other’s tech stack.
- Failures don’t crash the whole graph—graceful degradation is essential.
Case Example: Vendor Dispute Resolution in Supply Chain
A global manufacturing enterprise deployed an MACC to handle vendor payment disputes. Before the system:
- RPA bots flagged invoice mismatches.
- A ticketing system created cases in ServiceNow.
- Human agents triaged and manually escalated to procurement or finance.
Now, with an MACC:
- An LLM-based agent interprets incoming vendor emails.
- A retrieval-augmented generation (RAG) agent fetches context from previous conversations and ERP records.
- A task allocator assigns resolution to either a rule-based agent (for clear cases) or escalates to a human based on ambiguity scoring.
- If no response is received in 2 hours, a follow-up agent re-engages the vendor with templated messages.
Result?
- Resolution time dropped 40%.
- Human involvement fell by 60% in low-risk cases.
- All actions are audit-tracked, with clear accountability.
Final Considerations
In short, building a Multi-Agent Control Center isn’t just a tech project—it’s a strategic capability. It sits at the intersection of AI, operations, governance, and enterprise architecture. And it’ll likely become table stakes for any serious digital enterprise in the next five years.
Because in complex systems, autonomy without coordination isn’t just inefficient. It’s dangerous.








